What is secure about the OSSC
The OSSC has been developed with security being the hallmark of the environment. Security measures in place:
End-to-end VPN from CBS RA (Remote Access environment) to OSSC (@SURF) use case (project).
Sandboxed secure virtual cluster per use case (project).
Sandboxed storage solution, only accessible through OSSC (@SURF) virtual clusters.
Sandboxed separate InfiniBand partition for OSSC (@SURF) low latency communication.
Up-to-date virtual clusters, OS patches applied.
Firewall enabled, only traffic allowed between CBS and SURF through VPN.
Filesystem audit logging.
Linux syslogging.
Pentested by external security audit company.
All these measures ensure that data cannot leave the environment, except back and forth between CBS RA and SURF through the VPN. Thus conforming to the requirements set by ODISSEI, CBS and SURF.
How can the OSSC help my research project ?
The OSSC is meant for researchers performing analyses on highly-sensitive data, usually CBS Microdata, who need access to more computational power. The OSSC gives the possibility to leverage the compute capacities of the Dutch National Supercomputer (Snellius, SURF) to perform these analyses when available computing power at CBS is not sufficient.
All the compute capabilities of the Dutch National Supercomputer available to regular SURF users can be made available in a secure environment in the OSSC with a direct secure connection to CBS.
Typical user workflow
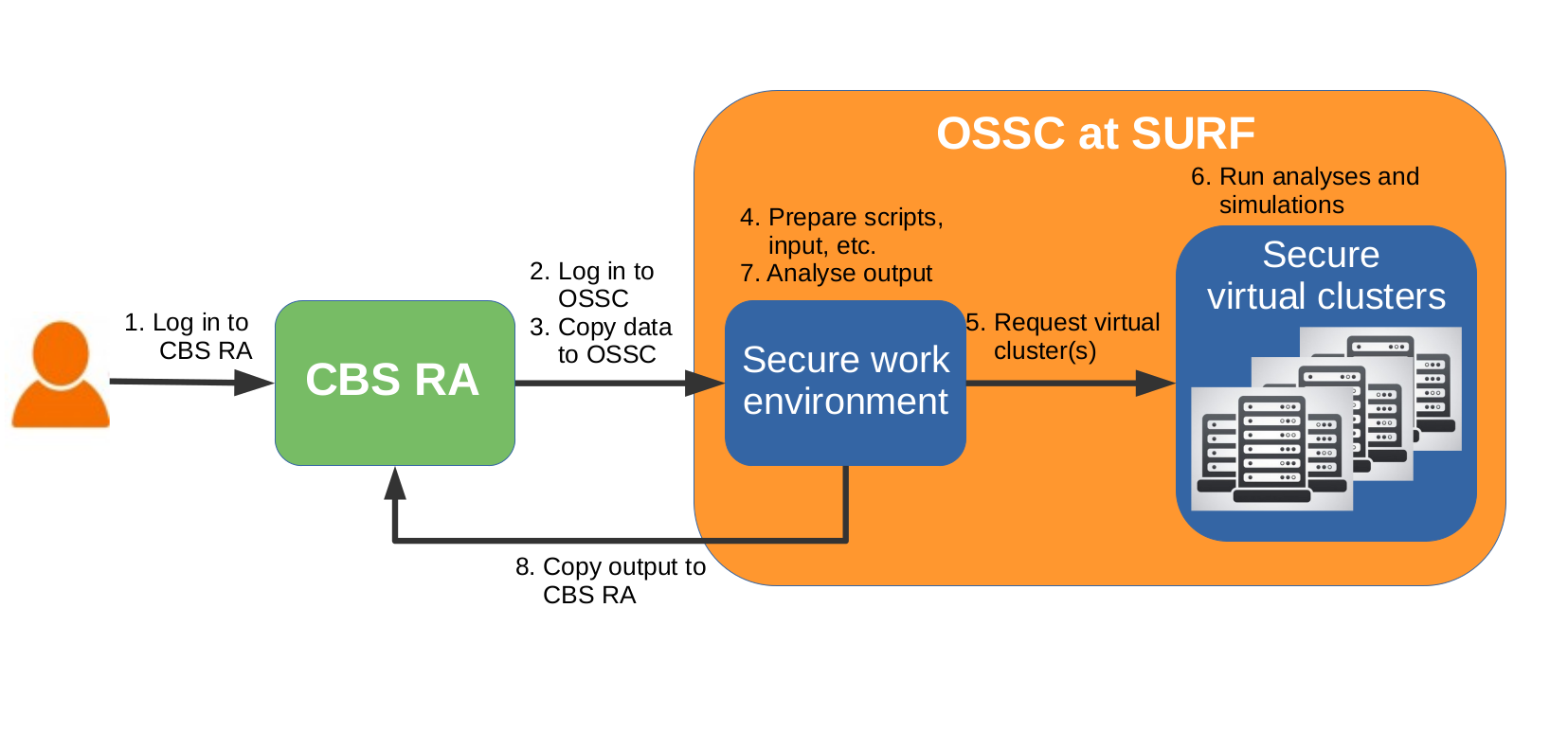
The high level steps to take in a project on the OSSC are the following:
- Log in to the CBS RA environment
- From the RA environment, log in to the OSSC
- Copy data to the OSSC
- In the secure work environment, prepare scripts and input, compile software and run lightweight tests. Request additional software and packages if needed
- Request a secure virtual cluster to get access to nodes dedicated to the computationally intensive tasks
- Run computationally intensive analyses and simulations jobs with Slurm on the secure virtual cluster(s)
- Check the output of the analyses on the secure work environment
When all computations and analyses on the OSSC are finished, copy the output to the CBS RA environment
The secure work environment is accessible at anytime during the validity of the project, and secure virtual clusters can be requested as many time as needed (within reasonable limits) as long as the user has sufficient available budget. |